
We also know that patching is not always possible, or even practical, in a complex production environment.
New vulnerabilities are discovered every day but, unfortunately, vendor-issued software patches are not always available. As a result, IT teams struggle to keep pace with traditional patch management strategies along with all the other business constraints.
Virtual patching creates a security shield around applications that require protection. Virtual patching establishes a security policy that identifies and intercepts exploits of vulnerabilities before they reach the target application.
Origina’s Vulnerability Shielding uses a specially compiled version of the open-source ModSecurity Web Application Firewall in combination with the standard OWASP Core Rule Set. Additional custom virtual patches are provided by Origina for any vulnerabilities not covered by the standard OWASP Core Rule Set. This solution provides a highly effective and agile patching solution against web-based vulnerabilities that protect your IBM® software programs.


Our Vulnerability Shielding service provides several distinct advantages over vendor-supplied patches in helping you to defend against known and emerging security vulnerabilities.
Patches for new security vulnerabilities may not be available from IBM for End of Support (EoS) product versions.
Patches for new security vulnerabilities may not be available from IBM for End of Support (EoS) product versions.
If a patch is available, it may not be released for several weeks or even months after the identification of the exploit. IBM’s X-Force 2012 Mid-Term Risk Report identified that 42% of all vulnerabilities disclosed that year still had no patch available at year end.
Development of a virtual patch for our Vulnerability Shielding solution can be completed in a number of hours rather than the days or weeks it can take to develop a patch using traditional coding methods.
Products divested to another vendor and source code not available.
Origina’s Vulnerabiltiy Shielding provides a solution to mitigate new and existing vulnerabilities without requiring modifications to the software program being protected.
The patching process is notoriously time consuming, requiring assessment, analysis, testing, remediation, and implementation.
Simplified implementation methodology involving import and activation of virtual patch rules.
The business impact of planned, or unplanned, downtime can be costly for a business, in terms of lost revenue, reduced user productivity, brand damage, and more.
No requirement for system downtime or prerequisite software patches. Virtual patches can be imported and enabled seamlessly while systems remain online.
Security updates come as bundles and can therefore affect existing services and must be rigorously tested. Bundled fixes can require upgrades or the reconfiguration of systems/ applications to resume required functionality.
Virtual patches are detection rules designed to identify a specific attack vector and do not interfere with the software program code base, unlike traditional software patches.
Origina arranges installation of the ModSecurity engine by using one of two deployment methods, either embedded in your environment or configured as a reverse-proxy. We then import and configure the OWASP Core Rule Set into the modSecurity engine. When enabled, any vulnerabilities that are identified in the data stream are mitigated before they reach the target application by using the appropriate virtual patch.
For IBM applications that are not covered by the OWASP Core Rule Set, custom virtual patches that are created by Origina can be imported to provide continued protection against new and emerging threat
The embedded mode deployment option configures the modSecurity engine as an IBM HTTP Server module on the server that needs protection. This option is the simpler method, as it requires no additional changes to the environment to enable the defense and virtual patching capabilities for applications.
Reverse-proxy mode deploys the ModSecurity engine on its own server, or virtual machine, in the data path in front of the applications that you want to protect. Although this option requires changes to the environment, the option has a number of advantages. Benefits include the ability to protect a number of web applications running on various operating systems, ease of administration, and protection when the embedded option is not available.
Vulnerability Shielding is effective in defending against known vulnerabilities where a patch is not available from the vendor.
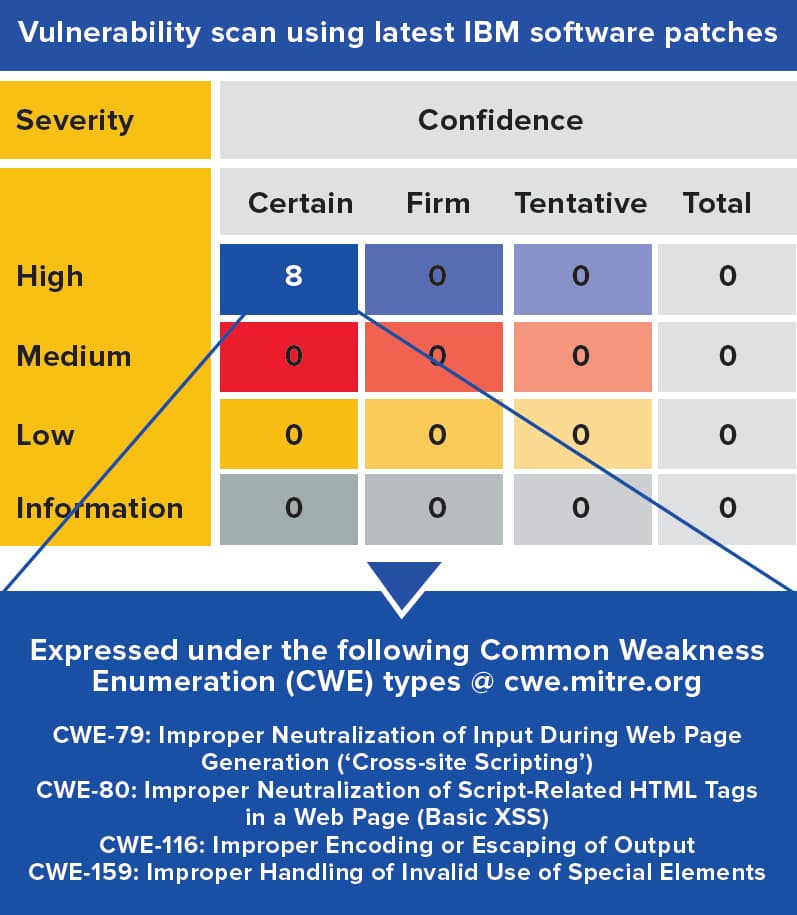
In this example, the latest, fully patched version of IBM® Websphere® Application Server v8.5.5.17 is deployed within the customer’s environment to host business applications.
The customer performed a vulnerability scan of the server and discovered eight high severity vulnerabilities.
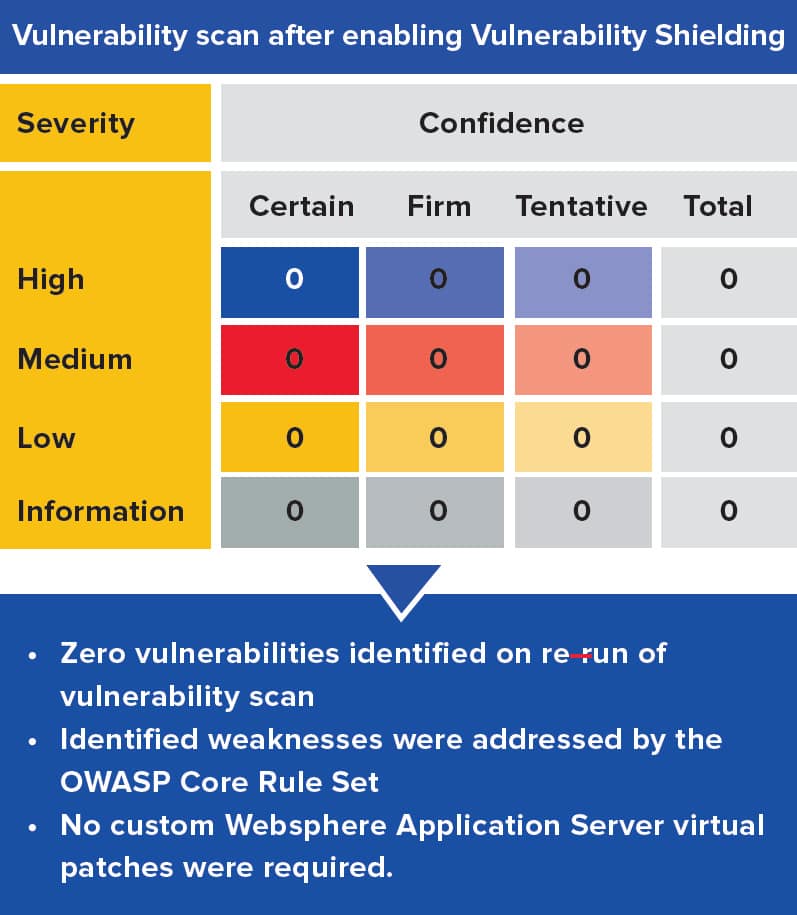
Origina’s Vulnerability Shielding was deployed in embedded mode and enabled with just the OWASP Core Rule Set. When the vulnerability scan was repeated, zero vulnerabilities were reported because the virtual patches mitigated the vulnerabilities before they reached the software applications.
See how much you could save by switching to Origina
upgrade your support