Can’t Trust IBM Software Maintenance from a Third Party? Separating Fact from Fiction
November 30, 2023
15 min read
November 30, 2023
15 min read
By Rowan O’Donoghue
Chief Strategy Officer and Co-Founder, Origina
It still astounds me the thinking and conventional approach that is applied to the management of IT assets. Yet at the ITAM Review Wisdom APAC Conference in Melbourne, Australia, I heard multiple organizations cite the same countless challenges they have around vendor audits, end of support (EOS) policies, the problems discovering what assets are even in the data center, managing staff behaviors, and the good old “we need to do more with less.”
I very much admire the work Martin Thompson and Rich Gibbons are doing with their teams to elevate this subject and bring professionals together to network, share challenges, and learn/adopt new ways of addressing all these challenges. I was delighted we were offered the chance to sponsor and participate in such a great event.
After spending the last decade architecting and designing our service offering, the majority of my time is spent these days helping organizations understand the value of our service and how it offers both choice and unquestionable value. Interestingly, over the past 12 months, I’ve noticed a sizeable increase in the aging rhetoric from IBM pushing forced upgrades and trying to cast a shadow over third-party software maintenance (TPSM) as a credible alternative.
One of my teenaged children asked me recently, “Dad, what is the single most important life-learning lesson you’ve learned?” It took me a few seconds to compose myself realizing how fast they had grown up, and another few seconds to ponder the question, but unequivocally I responded with “Fear. I’ve learned it has a nasty habit of preventing people from realizing their dreams with missed opportunities, both personally and in their professional career.”
There’s no better way to tackle some of these myths about TPSM than to talk about the fear behind these perceptions.
Even today, I still exhibit a small cheeky smirk when I get presented with this one. When Tomás O’Leary came to me back sometime in 2011 with his mad ideas on the back of a business trip to London identifying the emergence of the third-party software maintenance market and saying we were going to do it for IBM software, I dismissed it with a laugh-out-loud moment saying it was impossible.
My response mirrored the daily IBM customer rebuke of “There’s just no way to solve software defects without modifying the source code.” I, like everyone else, had been conditioned into a way of thinking because of how I had been brought up within the IT sector.
It played on my mind for months as I challenged myself. Why couldn’t we?
I recalled all those years as a senior engineer installing and supporting IBM software in the data center collecting emotional scars as frustration got the better of us when the software didn’t work. What did we do back then when there was no fix for IBM software defects? Corporate amnesia aside, we developed a workaround. Workarounds came in various shapes and sizes from configuration changes, shell scripts, or even changes external to the product at the operating system level.
Today, when we come across a validated software defect, we first identify if the customer is already in possession of an entitled IBM software fix to address the issue. Many IBM customers still forget that with perpetually licensed software products, they don’t lose access to all those fixes that were made commercially available up until their S&S expiry date, but they do need to capture them before then.
In this sample, the customer-identified defect was relatively simple, but it’s a good one to highlight the type of issue people would think is next to impossible to resolve without modifying the source code. In this case, the highlighted hidden radio box would not work when the administrator selected it, which resulted in sensitive information being displayed to end users.
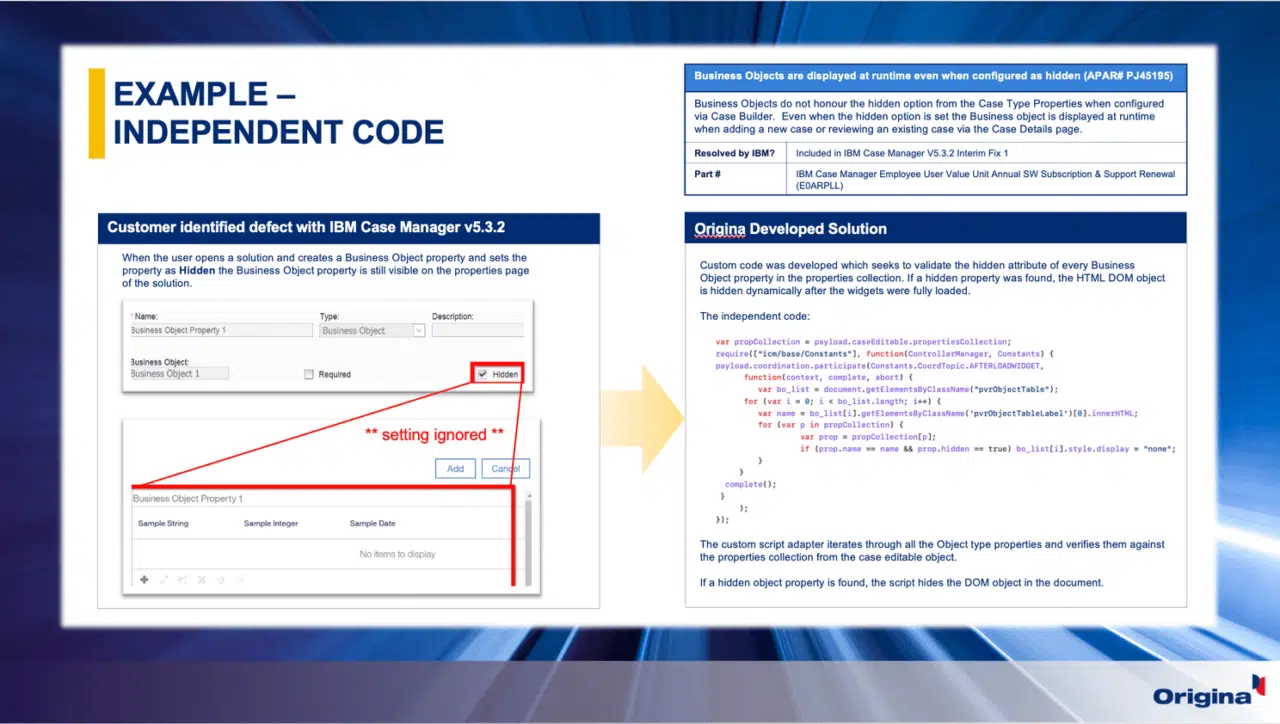
The customer was not entitled to an IBM fix, but it’s important to note that IBM did release one some months after the customer let their S&S lapse. We then set about identifying the most appropriate independent solution. In the majority of cases, code is not required since a simple configuration change could resolve the defect. In this case, that was not an option, so we developed code that was independent of the product’s source code.
By leveraging APIs in the IBM Case Manager product, our independent code is called and overrides the default functioning of the product to ensure the radio box works as originally intended.
Of course, I’m simplifying things to emphasize the point, but this would not be possible without the expertise and skill of our independent Global IBM Experts (GIEs). Having the experts who originally wrote these software products allows us to quickly identify how best to create solutions like this to minimize disruption for our customers.
Unfortunately, the real truth is you are going to be audited regardless of whether you are with Origina or not. That poses a more important question — are you compliant with your IBM licensing terms?
I really do empathize with customers when it comes to IBM licensing; it really is complex.
Coming from our old IBM business partner business, we thought we knew everything about IBM licensing. We were wrong, very wrong! Before we even launched our TPSM service offering to the market, we spent two years reviewing all of the IBM licensing agreements in detail. I quickly came to the realization that we would need to have a strong portfolio of licensing services as part of the overall offering to help our customers. Hands down, we have some of the world’s finest IBM licensing experts.
Today, our licensing services nearly outweigh our technical services in terms of customer demand. Our independent IBM License Validation Service ensures every customer has a 100% accurate Effective License Position (ELP). Would it shock you if I told you that if you’ve been transacting with IBM for 10 years or more, nine times out of 10, the entitlements listed in your Passport Advantage portal are incorrect? IBM hasn’t done a great job of accurately calculating changes with product evolutions and metric ratio changes over the years.
Our Audit Defense Service guides customers through the IBM license audit to ensure a successful outcome. This is delivered by ex-IBM license auditors who are well-versed in the dark arts tactics used to identify noncompliance.
Our IBM License Metric Tool (ILMT) services help customers make sure they are accurately reporting on usage consumption. For those IBM products ILMT cannot measure, our independent Global IBM Experts help interrogate the products to pull the statistics for accurate reporting.
Every day we help our customers cultivate a better understanding of IBM licensing terms and the pitfalls to watch out for. Most importantly, Origina provides confidence in their license compliance. Wouldn’t you rather be with a partner who has got your back?
It really worries me that organizations think they are safe from vulnerabilities just by applying the latest security fix. Security is much larger than a software fix. Cybercriminals are constantly evolving their skills and becoming more sophisticated in their efforts, and so, too, must we when defending against them.
I’m very proud of the significant strides we have made in developing our security services to provide that much-needed confidence to our customers by keeping their IBM software estates secure. It’s worth noting that 75% of the vulnerabilities we work on relate to the open-source components that are bundled with IBM software products, not the IBM software itself. When it comes to bundled open-source components, we are not restricted by the same intellectual property policies.
The first example that addresses this myth is the Log4J vulnerability. A combination of our extensive cyberthreat intelligence, IBM licensing knowledge, Global IBM Experts, and security teams allowed us to quickly pinpoint which IBM products, and, more importantly, which versions were exposed. Then we quickly developed mitigations for our customers, all at a time when the IBM support website stated they were working to figure out which of their products were affected.
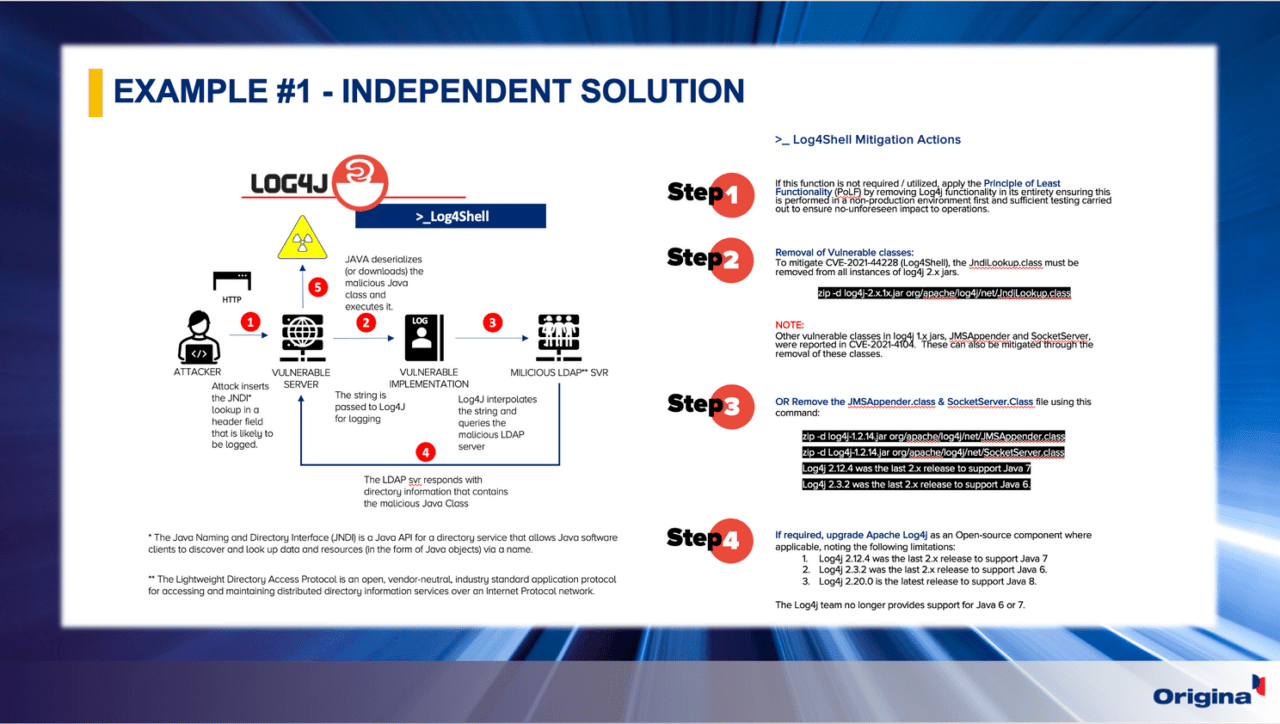
Our Vulnerability Advisory (VA) portal is the equivalent of the industry’s CVE databases. The moment we identify the emergence of a new vulnerability that impacts an IBM software product through our cyberthreat intelligence, we work on mitigations that then get published on our VA portal to ensure customers get timely mitigations to neutralize the threat.
Remember, unlike IBM, Origina doesn’t restrict which product versions we support, so all versions, regardless of IBM EOS status, receive full support.
In the second example from the ITAM presentation, I walked through a customer example for WebSphere Application Server. They had the latest IBM fix pack applied (8.5.5.17), and a vulnerability scan by the customers’ internal security teams identified eight high-risk vulnerabilities. In this scenario, we used our Vulnerability Shielding Solution to neutralize all of these vulnerabilities.
In recognition that a situation might exist in which we may not be able to address issues using independent code we developed our own solutions to mitigate emerging cyber threats. Our Vulnerability Shielding is one such solution focused on web-based vulnerabilities. Working much like an anti-virus program, it sits in the data path in front of the system and is protected. Once it identifies the signature of a known vulnerability, it has a corresponding payload to neutralize the vulnerability before it gets to the software application.
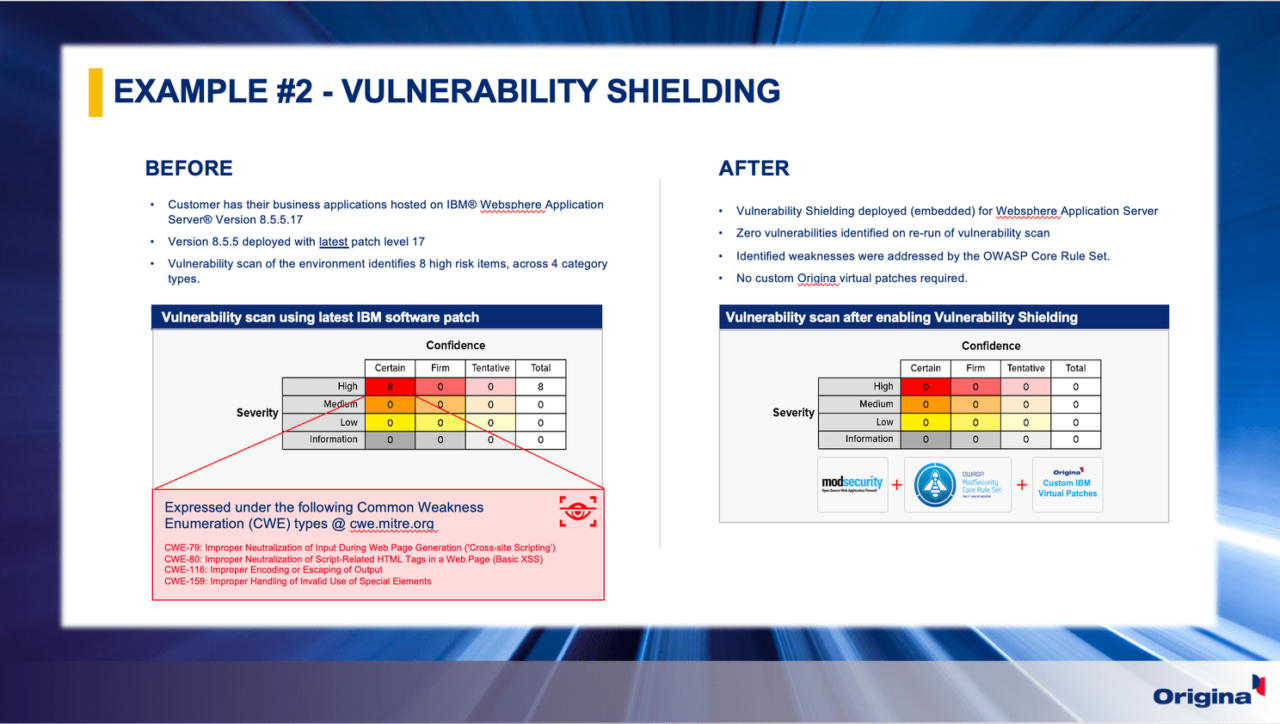
Security fixes don’t always come from IBM to resolve vulnerability issues, and if they do, they might not be timely. In this case, the customer had applied the latest IBM fixes and thought they were protected. I hate pointing it out, but this “tick-box” security approach is flawed.
This brings us back to my point about security being bigger than a patch.
I shared another statistic that shows that 85% of known vulnerabilities can be mitigated today just by employing proper hardening procedures. During the initial commissioning of an IT system, there is a lot of focus on security The problem is that over time, erosion of the security posture takes place due to upgrades, configuration changes of the software, and even new fixes (some fixes resolve the issue but introduce new ones). In short, a lot of weaknesses creep in that can present countless opportunities for a threat actor.
And it’s not just configurations. It’s the behavior of staff (one of the challenges mentioned at the event). I recalled an example of another IBM customer who was adamant they needed to stay with IBM for security fixes. In a brief review before the meeting, we were able to show that some of their IT staff were opening and sharing configuration files on public forums to assist in troubleshooting technical problems. Again, not malicious, but it emphasizes how threat actors can take advantage to quickly compromise a system — and not something an IBM security fix is going to prevent.
I get it. It’s an easy thing for me to say we can support all versions for as long as you need, but the reality is it is a much more difficult thing to deliver.
As one IBM customer pointed out to me recently, “Love the concept Rowan, but this is simply impossible due to the change that occurs in their IT environment.” Sure, they might be happy with the version of the IBM product deployed, but the issue is with the upgrade of the third-party vendor software products that interface with that IBM software product, all of which drag the IBM product on the upgrade escalator.
Anytime there is a need to upgrade software products in the data center, the technical teams consult the vendor Interoperability Matrices or Software Product Compatibility Reports. These show which IBM software product versions are compatible with third-party software versions. When the older IBM software version is not listed, the customer is forced to upgrade the IBM software product to maintain support.
Now, let’s think about this for a second. First, just because the older IBM software version is not listed in the Interoperability Matrix does not mean it will not work, just that IBM has not validated the interoperability in the labs. Second, remember that these interoperability matrices are only updated for products that are currently supported by IBM, not for EOS versions.
This is why we designed our Interoperability Validation service. It is designed to prove older IBM software product versions will work with newer third-party versions. In very simple terms, two things happen. First, our IBM experts demonstrate the correct functioning of the older IBM software product with the newer third-party product version. Second, the customer carries out a user acceptance testing program to confirm everything is working okay. When both teams give it the green thumbs up, Origina supports that configuration for as long as the customer requires. Once I explained the service and the process, it made sufficient sense for them to move forward being a customer.
It’s a good example of demonstrating how we extend the longevity of the IBM software asset.
I’m always curious to understand what’s behind a question. Every decision we make in life has consequences and carries risks. There is no such thing in life as zero risk. I could walk across the road from the office and get knocked down, but I’ll mitigate that by recalling the safe crossing code that was drilled into me as a kid and only cross at the pedestrian lights.
Yes, of course, there is some risk in moving your support to Origina, but the risk of remaining with IBM, I would argue, is much higher.
But I do understand the concern. The Origina value proposition looks like a great opportunity, but customers worry the business will change its mind in seven months’ time when the technical teams will say they need to upgrade to get a new technical feature.
You can always go back to IBM (not that you’d want to) if the business changes its mind. That door is not closed. In fact, you can be sure that IBM would be only too delighted to win you back from Origina, so you have a strong negotiating position to avoid any potential reinstatement charges. Also, we can help you understand what those reinstatement charges would look like before you move to Origina.
In the unlikely event you ever did need to go back to IBM, don’t forget that any new version would be at least 18 months from your S&S expiry date. You’d never upgrade straight away to the first major release, so your technical teams would probably have to wait a year for the first batch of fixes to come out for the new version to ensure stability, and the upgrade will probably take about another 12 to 18 months to carry out. You’re already in net savings territory if you moved to Origina and went back to IBM.
Remember, we offer customers choice, a choice that was not available until we came to market with our service offering. We allow IBM customers to break free from the restrictive support policies that force customers on an upgrade escalator just to get support. How does software become obsolete anyway and who makes that call? You? IBM?
You should only upgrade to obtain a new technical feature. By the way, chances are we could probably create that new feature for you using our Feature Enhancement service, allowing you to avoid the upgrade.
And remember, any change in an IT environment carries substantial risk. We’ve all witnessed numerous high-profile news stories with CEOs losing their jobs and huge fines levied on organizations due to these outages. Being forced to perform these upgrades just to get support is absolutely ludicrous.
Just as I was boarding the flight to Melbourne, one of our sales team members in the U.S. gave me an update on some of IBM’s ever-changing sales tactics to keep customers on this escalator. The IBM customer had received an extended support renewal for an EOS version of Maximo and paid these fees to IBM. IBM credited back the fees to the customer citing that they would not accept the payment for support unless the customer provided them with a written statement outlining when they would upgrade to a supported version.
Long story short, the customer had no plans to upgrade the version they had deployed and was unaware they had any options other than IBM until one of our partners introduced them to Origina.
Kinda begs the question, who is really locking you in?
I must admit, I do have to concede on this one and wholeheartedly agree — because it’s worlds apart.
There’s a common misconception that our support is just Technical Support. From the moment I went about designing our service, the mission was always to prove how much more valuable our service could be over what IBM provides. It draws upon years of experience working with customers to understand their needs and wants, while at the same time experiencing the decay in the value of IBM’s support.
To shine some light on what it really looks like I spoke about the recent accolade we were awarded by one of our customers in the U.K., Sainsbury’s.
In many respects, Sainsbury’s story is much like many of our customer narratives. During the initial conversations, the procurement and software asset management teams could see the significant opportunity Origina was bringing to the table, but there were some blockers to overcome.
You’ll never be able to provide better support than IBM. Fearing a decision just made solely on cost, Sainsbury’s chief technical architect cited concerns about the move. I personally went to meet him on-site and listened to all of the valid reasons why he thought we could not provide the same level of support they needed, which included direct access to the IBM labs at Hursley.
That might have been so, but I was confident we had the best Global IBM Experts in the world for the products we were proposing to support for Sainsbury’s. I also knew those same IBM experts in our team were likened to Gods within the IBM technical community.
I empathized with their concerns but took time to explain our model and to show how it massively differed from IBM’s random resourcing model. We assign a primary and secondary IBM expert per product, who remains in place for the tenure of the support, which promotes knowledge continuity, speed of resolution, and call efficiency. Understanding that these IBM experts were available and dedicated to Sainsbury’s, his concerns dissipated for the most part.
We never had to fight with you to get you on the phone. Understandably though, a bit more convincing was required. Sainsbury’s preference was to do a trial run of the service to help make a final decision. A support trial for their products ran in parallel with IBM support for the remaining six months up to the renewal date. Sainsbury’s used it to log support tickets with both Origina and IBM to determine the final decision. It was interesting news at the time knowing that IBM was aware of this trial.
Fast forward six months without any feedback other than we knew we had put our best foot forward with the support. I’ll never forget a comment made by one of the senior execs in the meeting. Semi-joking, I posed the icebreaker in the meeting, “So, how did we get on?” only to be flabbergasted by the response. “Well Rowan, let’s put it this way…. let’s just say we didn’t have to battle with you guys to get your technical experts at the end of a phone.” To this day, I’ll never forget that response, but it’s something we hear pretty frequently these days.
Black Friday and Cyber Monday. The Black Friday and Cyber Monday sales events are a huge source of revenue for Sainsbury’s. In previous years, the IT architecture was struggling to cater to the volume of sales transactions, and as a result, outages occurred which resulted in a significant loss of revenue. The first order of business was to help stabilize and prevent those outages. Leveraging our Meet the Experts Service, we were able to propose changes to the IBM software architecture to increase transactional bandwidth and avoid potential outages over the weekend. In addition, we deployed a team of twelve of our IBM Global Experts on the ground in shift rotation over the weekend, which allowed us to quickly focus on getting systems back up and running if there was an outage.
The right answer isn’t always to rip and replace. With a successful weekend out of the way and a sigh of relief, the focus quickly turned to what would happen in 12 months’ time. Another vendor working with Sainsbury’s was taking the line that the current architecture was legacy and beyond its sell-by date and that a move to the cloud was the way to go. We challenged this proposition. Like many environments, there can be a premature knee-jerk reaction that when a system causes the problem, it is no longer fit for purpose.
In reality, the IBM software environment had performed admirably for the last decade when you consider it was designed for five or six years of transactional growth and that was 10 years ago. The core products WebSphere Application Server, Sterling Order Management, and WebSphere Portal managed everything from sales orders, order fulfillment, and logistics. Truth be told, there was nothing wrong with those IBM software products. They were perfectly fit for their purpose and up to the task of catering to Sainsbury’s needs. They just needed to be re-optimized for the next five to six years of business growth.
Future success requires a change in mindset. The Sainsbury’s “Save to Invest” award is a testament to the value we provide customers with every day. We help them avoid unnecessary wasteful spending and divert those funds to much-needed innovation to ensure competitiveness in the marketplace.
The team in Sainsbury’s were brave. They embraced an evolved way of thinking about how they managed their IT assets, which is very much aligned with the ITAM review’s messaging. They looked the heroes, but more importantly, they were curious. We all need to stop letting vendors fan those flames of fear and start taking control of our own software roadmaps.
If you’re curious to learn more, I’d really encourage you to watch this great video of a talk by Origina CEO and Founder Tomás O’Leary alongside Gillan Leicester of PwC at the Gartner IT Symposium/Xpo™ in Barcelona. It explains what motivates us at Origina and what’s behind the recent partnership with This Spaceship Earth. Gillian does an awesome job sharing her insights from a customer perspective and the activist mindset that has allowed her to deliver real value for the organization.
Gain insight into industry-only news, access to webinars, tips and tricks, blog posts, podcasts, and guides, surrounding topics like cybersecurity, reducing software support and maintenance costs and much more, all delivered to your inbox each month.
LEARN MORE